Let iBoot DVD stay in your CD Drive. Just restart the machine. There will be a boot prompt. You can remove iBoot and swiftly reboot the computer. And then set MAC OS X Snow Leopard DVD or CD on. IBoot 3.3.0 Download. IBoot by Pupilizer is a Chameleon Boot132 CD particularly intended to work with Intel CPUs. It empowers a basic circle swap-out for the Mac OS X Retail DVD, and a vanilla establishment.
iOS contains many layers of encryption. This page details how to remove the encryption wrapper around each file in the IPSW file. A decrypted ramdisk is required to obtain the key for the root filesystem, but not to simply decrypt it with an existing key.
For more history, see Firmware Keys.
- 1Ramdisks
- 1.43.0 GM/3.0
Ramdisks
This section details the decryption of the ramdisks in an IPSW file. The listed console commands are applicable to the IMG2 or IMG3 files under /Firmware also.
1.0.x
With the release of the iPhone, the IMG2 files weren't encrypted. So, in order to use them, all you need to do is remove the 2048 byte (2 KiB) 8900 header from the file. You can do this with either a hex editor, or open up a console and run dd(1)[man]:
Once the header has been stripped, you will be left with either an IMG2 file or a mountable HFS filesystem.
1.1.x - 2.0b3
With the release of the iPod touch, Apple added a layer of encryption around the IMG2. The decryption key wasn't obscured however, and a simple analysis of iBoot by Zibri revealed the 0x837 key.
In order to decrypt them, you need to remove the 2048 byte (2 KiB) 8900 header from, then decrypt the resulting file. You can do this with either a hex editor, or open up a console and run dd(1)[man]:
Once the header is stripped, you need to do the actual decryption. The ramdisk is encrypted using AES-128 with cipher block chaining (CBC). The key is the 0x837 key with no IV. To decrypt, open up a console and run openssl(1)[man]:
Once decrypted, you will be left with either an IMG2 file or a mountable HFS filesystem.
2.0b4 - 3.0b5
With the fourth beta of 2.0, Apple introduced the IMG3 file format, replacing the broken IMG2 file format. This format was soon reversed and img3decrypt[src] was created by Steven Smith (@stroughtonsmith) on 21 Aug 2008. His code was later implemented into xpwntool[src]. In order to decrypt an IMG3 file, open a console and run one of the commands depending on your program choice:
The IV and key for a specific firmware is available through the Firmware Keys page or from the Info.plist file underneath PwnageTool's /FirmwareBundles folder.
Once decrypted, you will be left with either a raw binary blob. If input was a ramdisk, output will be a mountable HFS filesystem.
3.0 GM/3.0
OS X Snow Leopard introduced the HFS compressed disk image. With 3.0 (what beta?), Apple began using Snow Leopard to package the ramdisks. This results in some zero sized files in the disk image if you don't use Snow Leopard or newer. A discussion on extracting those files is available on the talk page.
S5L8900
With the 3.0 Golden Master (7A341) and 3.0.1, Apple messed up and, instead of using the application processor-specific GID Key, used a pseudo-GID of 5f650295e1fffc97ce77abd49dd955b3 to encrypt the KBAG. This makes obtaining the keys for this version dead simple. Once you have decrypted the KBAG, decryption using the keys in it is the same as above.
S5L8720
Business as usual, but keys and IVs have to be decrypted on the device still, unlike with the new S5L8900KBAGs. Apple incorrectly assumed that by encrypting iBEC and iBSS they were being sly. They were not. You can decrypt those on a 2.2.1 aes setup no problem whatsoever.
Iboot For Snow Leopard
S5L8920
The iPhone 3GS firmware files are interesting. They have two KBAGs, which use AES-256 instead of the S5L8900 and S5L8720 that are using AES-128 still. The first KBAG has an identifier in it's header indicating that it is to be decrypted with the GID Key on SoCs that have a CPFM of 03 (Production & Secure), and the second seems to be for decrypting with SoCs that have a CPFM of 01 or 00 (Development & Secure or Development & Insecure), as the CPFM seems to change which GID Key it uses. CPFMs of lower than 01 are normally prototypes in the DVT stage or lower. For those that don't know how AES256 works, this now means that the first 0x10 bytes are the IV, and the remaining 0x20 bytes (not 0x10 anymore!) are the key.
S5L8960 and later
With S5L8960, Apple changed the file format to use IMG4 files instead of IMG3. Decryption can be performed by running the following in a command line application (make sure you have the img4lib):
INPUT is the file you want to decrypt, OUTPUT is the file you want to output once decrypted and ivkey is the IV and Key together for the file you are trying to decrypt.
SEP
This section details the decryption of the Secure Enclave Processor in an IPSW file. The listed console commands are applicable to the IM4P files under /Firmware/all_flash.
With the release of checkra1n 0.12.0, pongoOS has been updated to include Pangu's project blackbird which allows the exploitation of the Secure Enclave Processor to A10 and A10X devices (for now, others will be supported in the future) from iOS/tvOS 12.0 - 14.2. To decrypt it, you'll need to enter pongoOS and insert the KBAG. This is done by compiling the pongoterm binary from the checkra1n project pongoOS then execute a few commands in Terminal.
On macOS, if the checkra1n app is inside the /Applications folder:
/Applications/checkra1n.app/Contents/MacOS/checkra1n -cp
Alternatively, you could right-click the checkra1n.app and select 'Show Package Contents' then navigate to /Contents/MacOS/ and drag the checkra1n binary directly inside Terminal then adding -cp to the end.
Otherwise, with Linux you can install the latest via the repository then launching the checkra1n CLI:
sudo checkra1n -cp
Once done, use a USB to connect and place the device in DFU Mode. The process will begin with checkra1n running the device exploitation stages until a device boot is initiated. The Apple logo will show following the checkra1n logo shortly after along with some text on the screen. From here the user can execute the pongoterm command to enter the PongoOS shell.
Inside this shell you can type in sep auto which will start the Secure Enclave Processor exploitation process.
Then inserting the KBAG by typing in sep decrypt KBAG.
PongoOS will display the input KBAG from the IM4P file and output the decrypted IV and Key.
The iBoot + MultiBeast method is designed and tested for any desktop or laptop running the latest line of Intel processors, the Core i3/i5/i7s. I have had reports of success with older machines as well including CoreDuo, Core2Duo, and even Pentium 4. However, AMD processors are not supported.
YOU WILL NEED
- A computer running an Intel Processor
- A blank CD
- A Mac OS X Snow Leopard Retail DVD
- To leave any fear of your computer at the door.
- Patience and humility- it may not work out perfectly the first time- but with enough tenacity and grit, you'll reach the promised land. It's easy to get frustrated, but don't give up! There are a community of users with similar hardware in the tonymacx86 Forum to provide support if you get stuck.
- Use only 1 graphics card in the 1st PCIe slot with 1 monitor plugged in.
- Remove any hard drives besides the blank drive being used for OS X.
- Remove any USB peripherals besides keyboard and mouse.
- Remove any PCI cards besides graphics- they may not be Mac compatible.
- It's best to use an empty hard drive- you will have to partition and format the drive.
- Always back up any of your important data.
You will need to set your BIOS to ACHI mode and your Boot Priority to boot from CD-ROM first. This is the most important step, and one many people overlook. Make sure your bios settings match these. It's not difficult- the only thing I did on my Gigabyte board besides setting Boot Priority to CD/DVD first was set Optimized Defaults, change SATA to AHCI mode, and set HPET to 64-bit mode.
STEP 2: INSTALL MAC OS X
In order to boot the Mac OS X Retail DVD, you'll need to download and burn. For desktops and laptops using unsupported Intel CPUs and graphics, a legacy version of iBoot can be downloaded here. If you have an Ivy Bridge or Haswell system, you can’t use the default iBoot. Use iBoot Ivy Bridge
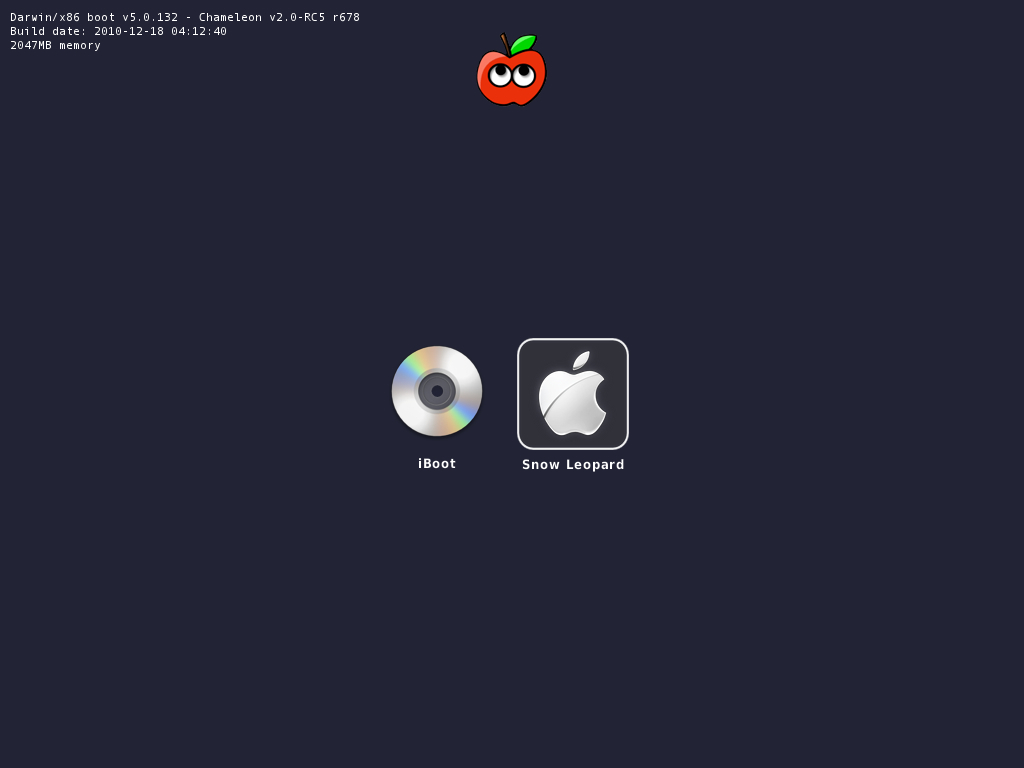 or iBoot Haswell.
or iBoot Haswell.
- Download iBoot
- Burn the image to CD
- Place iBoot in CD/DVD drive
- Restart computer
- At boot prompt, eject iBoot
- Insert your Mac OS X Snow Leopard Retail DVD and press F5
- When you see the screen below, press enter to begin the boot process
- When you get to the installation screen, open Utilities/Disk Utility. NOTE: If you cannot get to the installation screen, retry from Step 4, type PCIRootUID=1 before hitting enter. If that doesn't work then try PCIRootUID=1 -x or just -x which will enter Mac OS X Safe Mode and will allow you to proceed. For some graphics cards, use GraphicsEnabler=No boot flag to proceed.
- Partition your hard drive to GUID Partition Table
- Format your hard drive to Mac OS Extended (Journaled). NOTE: The bootloader can only boot from a disk or partition of 1 TB or less. Partition larger drives.
- For the purposes of this guide, name it Snow Leopard. You can rename it later.
- Close Disk Utility
- When the installer asks you where to install, choose Snow Leopard
- Choose Customize‚ and uncheck additional options. This will hasten the install process. You can always install this stuff later.
- Restart computer.
- Place iBoot back in drive.
- When you get to the boot selection screen, choose your new Snow Leopard installation.
- View the super-cool Mac OS X Snow Leopard Welcome Video, and set up your computer!
STEP 3: UPDATE TO 10.6.8
If you have a Sandy Bridge system, please follow these specialized instructions to update to 10.6.8.
- Open Finder and navigate to your Snow Leopard drive.
- Download the Mac OS X 10.6.8 Combo Update
- Download MultiBeast
- Open MultiBeast- don't run it yet, just leave it open. Set up windows as shown.
- Mount MacOSXUpdCombo10.6.8.dmg
- Install MacOSXUpdCombo10.6.8.pkg
- Upon completion, the installer will ask you to reboot. DO NOT REBOOT.
- Switch to the already open MultiBeast. If it closes, just re-open it.
MultiBeast is an all-in-one post-installation tool designed to enable boot from hard drive, and install support for Audio, Network, and Graphics. It contains two different complete post-installation solutions: EasyBeast and UserDSDT. In addition it includes System Utilities to rebuild caches and repair permissions and a collection of drivers, boot loaders, boot time config files and handy software.
Choose one of the following options directly following a fresh installation and update:
EasyBeast is a DSDT-free solution for any Core/Core2/Core i system. It installs all of the essentials to allow your system to boot from the hard drive. Audio, Graphics and Network will have to be enabled separately.
UserDSDT is a bare-minimum solution for those who have their own pre-edited DSDT. Place your DSDT.aml on the desktop before install. Audio, Graphics and Network will have to be enabled separately. HINT: Check the DSDT Database for a pre-edited DSDT.
- Run MultiBeast.
- If you have a custom DSDT that's been edited, place the file on your desktop and choose UserDSDT.
- All others select EasyBeast
- Select System Utilities.
- Optionally, you may install further drivers via Advanced Options to enable ethernet, sound, graphics, etc... Be sure to read the documentation provided about each installation option. NOTE:EasyBeast, and UserDSDT install the bootloader by default, so you'll not need to check that option.
- Install to Snow Leopard- it should take about 4 minutes to run scripts.
- Eject iBoot.
- Reboot- from your new Snow Leopard installation drive.
Your PC is now fully operational, while running the latest version of Mac OS X Snow Leopard! And you have a nice Boot CD to get into your system in case things go awry. Boot your system from iBoot if you have issues. You may run MultiBeast as often as you like.
Iboot Snow Leopard Gecko
If you can't boot, try typing -x at the boot prompt to enter safe mode, or just boot with iBoot. When you get to the desktop, you can make all of the changes you need to. The best way to start fresh is delete whatever you're trying to get rid of- including the whole /Extra folder, as most kexts are installed there. Then you can re-run MultiBeast. As long as you rebuild caches and repair permissions after you're done, you can do just about anything you want to /Extra/Extensions and /System/Library/Extensions. Anything can be tweaked and enabled upon subsequent uses of MultiBeast.If you've had success using iBoot + MultiBeast, consider a contribution to help keep the sites going. We're constantly updating and tweaking our tools to help you.
Thanks in advance!
-tonymacx86 & MacMan
For our most current workarounds and solutions forissues such as USB and audio, check out the Mac OS X 10.6.3 Update, Mac OS X 10.6.4 Update,Mac OS X 10.6.5 Update, Mac OS X 10.6.6 Update, Mac OS X 10.6.7 Update, and Mac OS X 10.6.8 Update
 articles. Good luck, and see you on the forum!
articles. Good luck, and see you on the forum!Related Posts: Dual Boot Windows 7 and OS X Snow Leopard
Iboot Snow Leopard Usb
